Did they really break RSA?
The Rivest-Shamir-Adleman (RSA) Encryption Algorithm
RSA is an asymmetric encryption algorithm widely used in many products and services. Asymmetric encryption uses a key pair that is mathematically linked to encrypt and decrypt data. A private and public key are created, with the public key being accessible to anyone and the private key being a secret known only by the key pair creator.
If the public key is used for encryption, the private key must be used to decrypt the data.
How it works
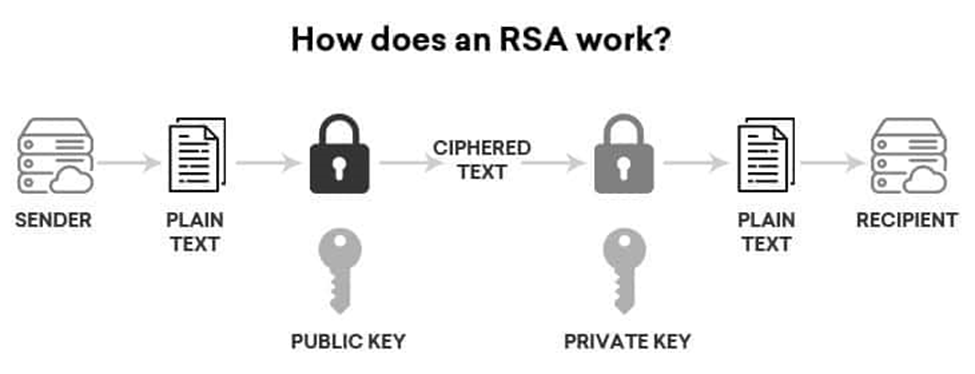
Key Generation:
- Alice picks two prime numbers: p = 11 and q = 13.
- She calculates n: n = p × q = 143.
- She calculates the totient: φ(n) = (p - 1) × (q - 1) = 120.
- Alice chooses e = 7 as her public key.
- She calculates her private key d = 103 using a special math method.
Sending an Encrypted Message:
- Bob wants to send a message (number 9) to Alice.
- He uses Alice's public key (n, e = (143, 7)) to encrypt his message.
- The encrypted message (ciphertext C) is calculated as: C = 97 mod 143 = 48.
Decrypting the Message:
- Alice receives Bob's encrypted message (C = 48).
- She uses her private key to decrypt it: M = 48103 mod 143 = 9 (the original message).
Digital Signatures:
- To sign a message, Alice creates a hash (a short summary of her message).
- She encrypts the hash with her private key and sends it with the message.
- Bob can verify the signature by decrypting the hash with Alice's public key.
- If it matches the hash of the original message, it proves:
- Authentication: Only Alice could have sent it.
- Integrity: The message hasn’t been changed.
Encrypting for Confidentiality:
Alice can also encrypt her message with Bob's public key for confidentiality.
Digital Certificates:
A digital certificate contains information about the owner and their public key. It is signed by a certificate authority, helping to verify public keys and their owners.
Encryption Strength
Encryption strength is directly tied to key size. Doubling key length can deliver an exponential increase in strength, although it does impair performance. RSA keys are typically 1024- or 2048-bits long, but experts believe that 1024-bit keys are no longer fully secure against all attacks. This is why the government and some industries are moving to a minimum key length of 2048-bits.
RSA Vulnerabilities
Weak Random Number Generator
When organizations use weak random number generators, then the prime numbers created by them are much easier to factor, thus giving attackers an easier time of cracking the algorithm.
Poor Key Management
RSA keys have certain requirements relating to their generation. If the prime numbers are too close, or if one of the numbers making up the private key is too small, then the key can be solved for much easier.
Side Channel Attacks
Side channel attacks are a method of attack that take advantage of the system running the encryption algorithm, as opposed to the algorithm itself. Attackers can analyze the power being used, use branch prediction analysis, or use timing attacks to find ways to ascertain the key used in the algorithm, thus compromising the data.
Did they really break RSA?
RSA Encryption has proved to be a successful method for protecting sensitive information, as it requires mathematical computation so complex that it cannot be solved by even the most powerful supercomputers in the world today — unless they have the cryptographic key.
I can't find any evidence to suggest that RSA has been broken. But they were able to break a 20 to 50 bits interger key
Do you think that the size of the key matters?
Yes , Size really does matter in encryption. The strength of an RSA encryption relates to the length of the integer which defines how big the problem is. For example, a 50-bit integer has 9.67 x 10^16 possible values.
Conclusion
But most modern encryption technologies now use 1024 to 2048-bit integers. A 1024-bit integer has 1.797 x 10^308 possible values, while a 2048-bit integer has 3.231 x 10^616 possible values. Hence, the number of possible values for modern encryption methods are immensely larger and, therefore, more complex than the one overcome by the researchers.